Gmail is the most popular email service to date, thanks to its creator, Google, the name which is often associated with user-friendliness and security. Despite what the company does to keep your emails safe,
you may still be preyed on by hackers, phishers and scammers from all over the
Web.
Well, the good news is that Google has been forging
its Gmail security system by adding new security features, most of which we do
not know about. Today we want to show you 10 essential, technical and
non-technical tips that will further strengthen your account security from
any possible threat and scheme.
While some of them might sound complicated at
first, their instructions are extremely easy and they can be completed without
any further study, so embrace them and you will prevent one of the worst nightmares
of your life – a Gmail breaking and entering
While some of them might sound complicated at
first, their instructions are extremely easy and they can be completed without
any further study, so embrace them and you will prevent one of the worst nightmares
of your life – a Gmail breaking and entering
1. 2-Step Verification
To combat the growing account theft issues, Google
has introduced a security feature which will greatly strengthen your account:
2-step Verification. In general, it adds
an extra layer of security by enquiring
a code that will be sent to your phone every time you request for the
account access, thus making it impossible for anyone to hack into your account
without your phone.
Sounds problematic? Probably not. The awesome thing
is that the setup is fairly easy,
you just need to visit the setup
page and follow a series of simple
instructions, and that’s all, you are good to go! In case you need
any troubleshooting in the future, you can also visit the Help
page to seek for a solution.
With this 2-step verification, you can even create a backup phone number and printable
backup codes as alternatives to access your account if you lose your
phone. For applications that cannot request for the verification code, you can
also create an application-specific password for them. So basically your account will be inpenetrable, unless your
closed ones betray you.
It might feel a bit annoying the first few times,
but it beats getting your account hacked and then getting blackmailed to regain
access to your own email account, doesn’t it?
2. Enable
HTTPS Security
When it comes to accessing your Gmail account in
public wireless or non-encrypted networks, HTTPS could mean your security. Leaving HTTPS disabled will only
make it easier for attackers to crack open a path into your Gmail account.
HTTPS is enabled by default, but past experience has taught me that it’s always
better to perform a check to ensure
that the HTTPS option is on.
To do the check, log into your Gmail account. A big gear-like icon will appear on the
top right side of the interface. Click on the gear icon > Settings > General > Browser
Connection and see whether the option, “Always use HTTPS” is checked. Remember
to save the changes!
By doing this, your account is potected by a secure
protocol that provides authenticated and encrypted communication. Oh, if you’re
doing this on public computer, do remember to log out of your Gmail account after using it!
3. Check Granted Account Access
The first thing you must check to see if you have
suspicious activities happening in your Gmail account, is probably your granted account access settings. I
guess if a hacker had a chance to infiltrate into your account, he will
probably add his own created fake mail account into your Gmail for easier
future access, or for a re-hacking session if his other tricks were exposed and
removed.
Well how can he do it? It’s really easy, he just
has to hack into your Gmail account, click on the gear-like icon, select the Settings
> Accounts and Import > Grant access to your account, then
add any fake email account into it. Now that you know the route, it’s your turn
to perform the steps mentioned above, except that instead of adding account,
you have to check if there’s any account you didn’t authorize access to
your Gmail.
Also, be sure that the option, “Mark
conversation as read when opened by others” is checked, so whenever someone
is reading your mails without authorization, you will know about it. Keep
your eyes peel for this option
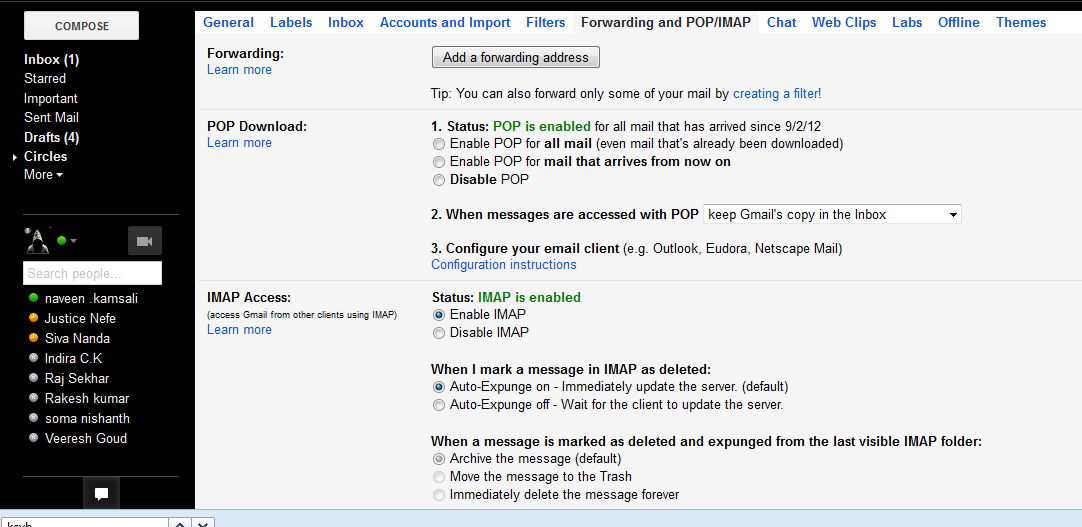
4. Check Your Filter, Forwarding
and POP/IMAP
In 2007, a famous designer, David Airey’s Gmail account is hijacked.
To make the long story short, the hacking started when the user has its account
signed on and he went to visit a bad site. The site added a backdoor to extract
information from the Gmail account, and the backdoor is the Filter. Filters
can potentially transfer emails as long as the victim has the filter in his
account
Therefore, it’s vital for you to actually check
your account settings to delete suspicious filters. The check is real
easy. As usual, you just need to log into your Gmail account, then after
clicking the gear-like icon, choose Settings > Filters to
check and delete the Filter you didn’t put there before.
You will also need to check the “Forwarding and POP/IMAP”
tab as well to confirm that there is no foreign forwarding address included in
this tab apart from those assigned by you. Do perform a check on these stuff
when you feel that something unusual is going on in your account. Your
prevention methods will save you from experiencing problems in the future.
5. Revoke Unauthorized Access
Just like what you did to most applications in
Facebook, you might have granted permission to any website or web application
that requested for access into your Google Account, and that’s one of the
hottest tricks that hackers use to access your Gmail.
Many Gmail users wouldn’t notice this security hole
easily, as the option comes from your Google Account, not your Gmail
account. And heck, it’s really easy to check if you’ve granted too much trust
in them: log into your Google Account, then access this page, and you will see a list of sites and/or web applications that you’ve
granted access to.
Click “Revoke Access” if you find any
doubtful applications, and it’s a good practice to revoke access to
any application that is unnecessary anymore, even if they are not harmful.
6. Track Account Activity
The best method to check if you’re actually hacked
is to know your account activity. Fortunately your Gmail is created by
the Google who can do wonders with security features. One proof of that is they
have developed an Activity Information panel for you to track your
account activities.
it’s really easy to access the Activity Information
panel. We may have even scanned through it all the time without actually
noticing it. Sign into your Gmail and on the bottom part of your mail, you
could see the message saying “Last Account Activity: (number) minutes ago“;
click on the “Detail” then you can see the access type, location
& date that you have signed into Gmail in past few days.
Under the panel you can also set the Alert
preference so Gmail could alert you when it detects certain unusual
activities. Be sure to always check the Activity Information panel any time you
notice any weird stuff happening in your Gmail.
7. Embrace security plugins
In the end, no matter how strong your security is,
you might end up getting tricked by phishers and scammers. To combat these
tricky situation, you can adopt browser plugins which will greatly
strengthen your online security by aiding you in recognizing phishing sites and
by removing threats, at the cost of hundreds of kilobytes!
Web of Trust (WOT) is an awesome browser plugin that checks whether you are accessing a
bad site. When you entered a potentially bad site, WOT will show you a dark
page covering the front page of the site, and inform you that the site has
poor reputation, while blocking you from accessing the page. WOT is
available for major browsers like Firefox, Google Chrome, Safari, and more!
On that matter, there is a double-edge sword called
cookies. It stores certain user information and preferences for convenient site
information access in future, but it also leaves a path for attackers to
infiltrate your computer. That’s when BetterPrivacy comes to the rescue. Basically it removes special long-term cookies,
thus greatly eliminating the chances for attackers to hack into your account.
Better Privacy is only available for Firefox, but
you can get similar plugins by searching your browser’s plugin store with the
term “privacy“. Other than that, you can browse the Firefox Add-ons Page, Chrome Web Store, Safari Extension Gallery or any
other browser’s plugin store to get more security tools for your browser. But
always remember to check the plugin before adopting it, as you might
know, sometimes the help could be the culprit itself!
8. Account recovery options
You will be surprised to the fact that hackers love to hack into your account from your mail
recovery’s security option, than to confront your already strong
password directly. It’s really reasonable though, since most websites teach you
to create a strong password, but they didn’t tell you to spawn a tricky on
account recovery option...
Use different email recovery
address(eg:use ur brother,sis,or blood friend email address) you can also use
an ALTERNATE email address if necessary
9. Create a
Strong Password
Unless you’ve enabled 2-step verification, your password is the only entity that guards
all your mails, contacts and sensitive information. In order to make your Gmail
account more invulnerable to the hacker, you need to create an invulnerable password.
Avoid easy passwords like “iloveyou” or “password”
or “1q2w3e4r“, all of these can
be easily hacked. That said, you shouldn’t create 3 kinds of password, which
are listed as below:
- Password which consists of words that can be found in dictionaries.
- Password which consists of words only or numbers only.
- Password which consists of your name or any personal information existed on web.
Now on the strong password creation, that’s a great
memory trick called Mnemonic, in which you utilize your brain function to remember a password. Let’s
say you want to create a long password, you can use a sentence like “icreatedthisaccountin2012“. But the
password is too long and it still can be hacked easily, so you can take the first letter of every word and
combine with the numbers to become something like “ictai2012“.
Well, it’s not really a strong password, so you
should add in your own “unique symbol”
like @ on every 2
letters/numbers, which becomes “ic@ta@i2@01@2”
(please don’t adopt this password since we explained it here). This should look
safe, and it takes short time to master.
Be creative! Otherwise you can go hardcore
by creating 24 keys password with
random words, numbers and symbols, and try to memorize it every day.
Normally this only costs you around a week to get well-accustomed with it.
You’ll be surprised at how fast you can memorize it since your brain is forced
to retrieve this essential information every time you want to access your
important account.
After you’ve set up your password, you can test
your password’s strength directly though The
Password Meter, and also possibly obtain some
valuable tips from the site.
10. And Never Trust Anyone
Even (and especially) when you receive emails from your loved ones, because their account might be hacked and those emails are actually
sent not by them and without their permission. I believe that most people
already know about this but I feel it important to list this advice down
nonetheless.
The fact is that I can’t really count how many scam
or phishing mails I’ve received from my friends’ hacked accounts. Fortunately I
was calm enough to not open the “I love you” email, but there could be certain
mails like “Robbed in China” scams in which "your friend" asks for
your emergency help, and these are the ones that could really trick you as the
request for help is coming from your dear friend.
Normally your first reaction would be to ignore the
mail, but if you’re really curious about the situation, then reach out to
the friend or his/her family members to verify the crisis before
extending any help . Otherwise, you’re the one who will face the crisis, so
please keep the warning in at the back of your mind any time!

















0 comments:
Post a Comment